The DTS Cyber Security team receives many reports of phishing. Fortunately, many users correctly identify phishing & don't take the bait! This bowl is full of real phishing examples reported at our School. Swim back soon - we regularly find new species of fish!

Eventbrite phishing
Phishing emails purporting to be coming from Eventbrite are targeting departmental/divisional inboxes, prompting users to click on a link to process a refund. The links do not lead to an eventbrite site, instead, it’s probably something malicious or undesirable.

Twitter link phishing
Very short emails with little context, usually coming in twos. The first email contains a shortened twitter URL that starts with https://t.co/ and the second prompts the recipient to check out the link as it may interest them.
Read more here


Predatory conference/journal scams
These scam emails will urge you to submit an abstract or researcher profile, or register as a speaker at a conference.
Often, the following signs will tell you a conference or journal email is fake:
-
The language is overly generic, e.g. ‘Climate Change Conference’. ‘Dear Author’
-
It has a website presence, but lacking in photographic evidence or sponsors
-
It requires you to pay a membership/registration fee


Spyware blackmail
These are strongly worded emails that claim they have spied on you with malware and demand payment of cryptocurrency or risk having all your personal data leaked onto the dark web.
Some users were concerned about the source email looking like it was coming from them. However, this is because the email was spoofed, meaning the sender address was manipulated by the sender to appear differently from the real source.

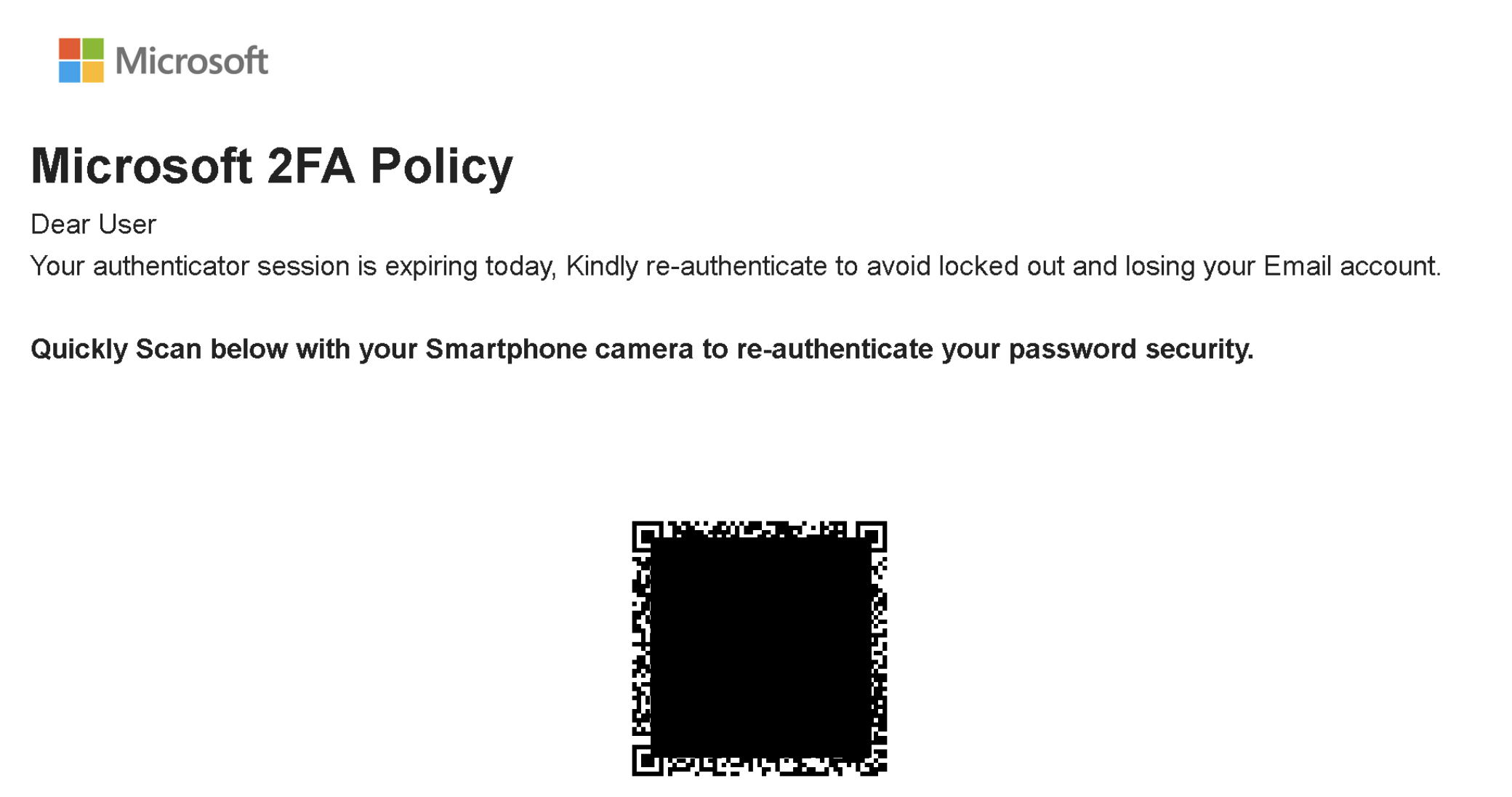
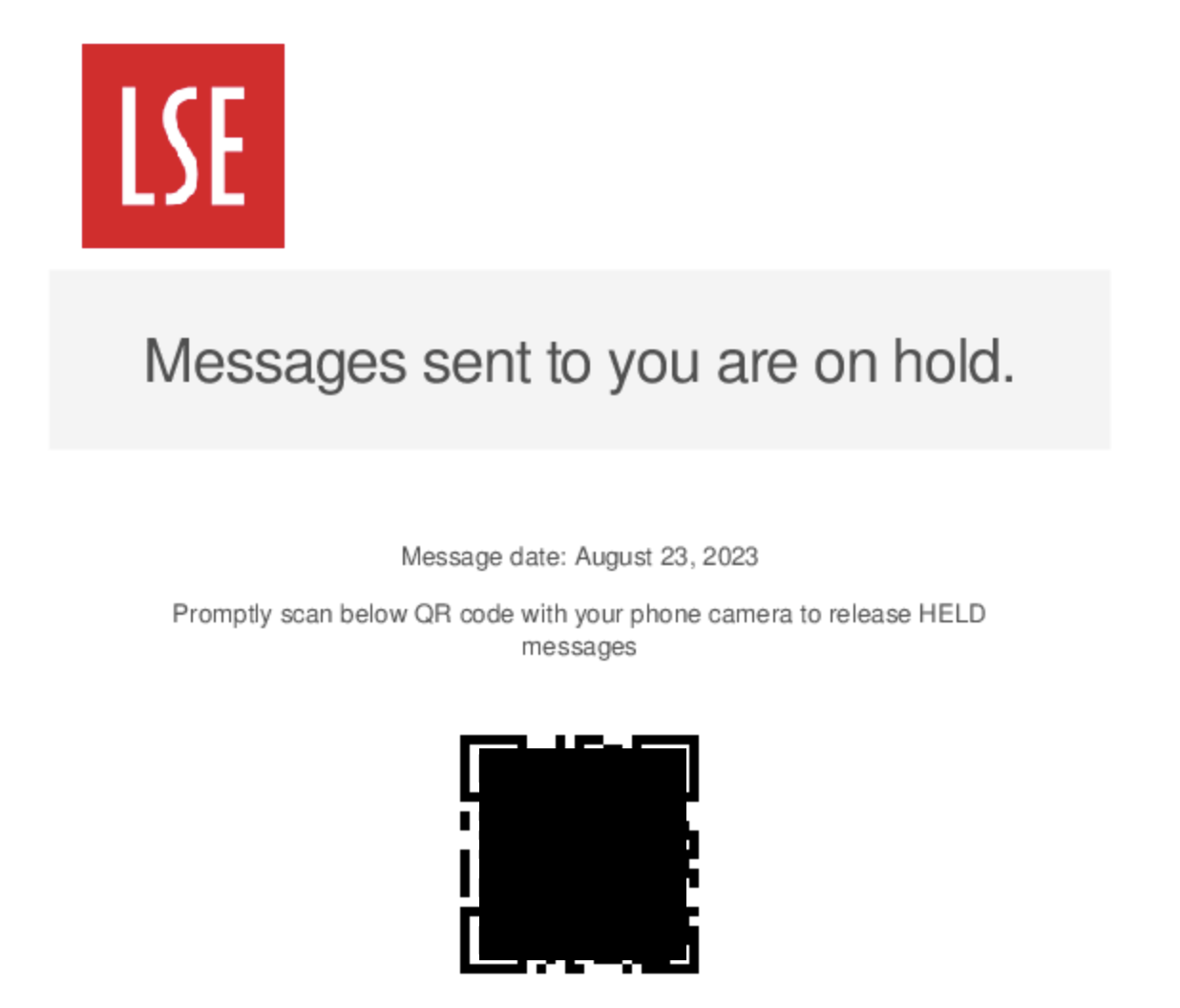
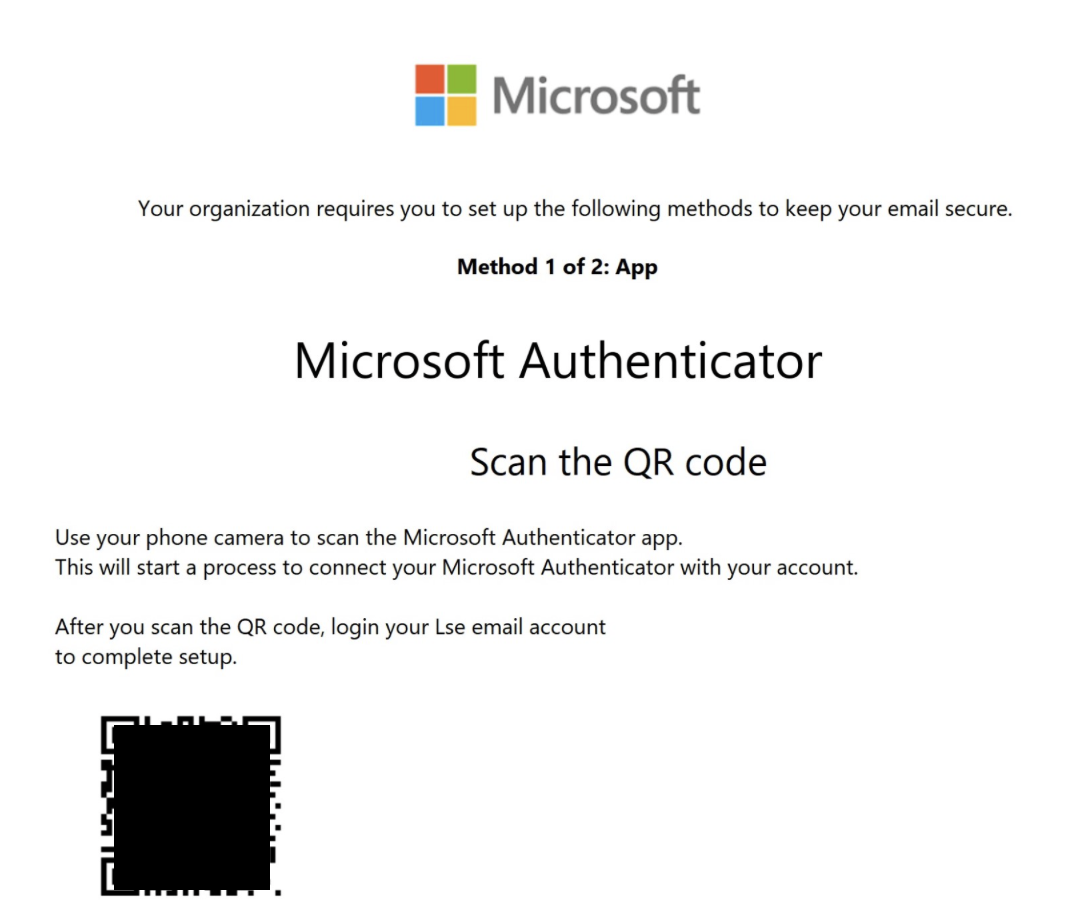
QR Code Phishing
QR code phishing emails are trying to compromise your LSE login credentials. Typically, they show a QR code (redacted in the following examples) for you to scan with your phone, and after asking you to input your LSE password, they will attempt to bypass your MFA.
Read more detailed advice in our blog article here.
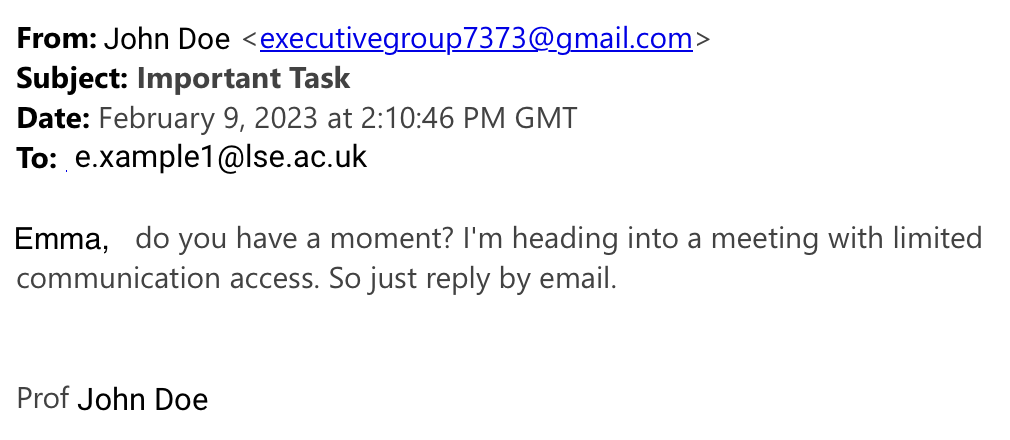
Email: Important Task
Recently, there has been a notable uptick in emails purporting to be an LSE staff member, contacting other LSE staff in their department/division. The sender is usually a Gmail, iCloud, or other generic email address, not the real @lse.ac.uk of the person being "spoofed" or impersonated.
The subject line varies, we have seen reported examples of "Important Task", "Waiting for your quick reply", "Hi", and "URGENT!!!"
These types of phishing emails are mainly financially motivated - the bad actor wants you to purchase a gift card, worth hundreds of £, and send them the code on the back of the card to redeem.
If you provide your phone number, you will likely be targetted by future phishing campaigns as a potentially suseptible target. If you share your phone number, we strongly recommend removing it as an MFA method for your LSE account.
If you are "spoofed" - meaning a phishing email is circulating pretending to be you - this does not indicate your LSE account is compromised. The best thing to do is warn your colleagues in your team/division and report the phishing email to phishing@lse.ac.uk.
Tip: Check the sender line before replying, especially on your phone! The mobile app for Outlook does not show the sender's email address immediately, unless you tap.
Your Password's Changing!
DTS will never contact you via email to say your password is expiring. As of November 2021, periodic password changes are no longer a part of the School's Password Policy.
Tip: If you're told your LSE account will be disabled within 24 hours and all your data will be wiped and unrecoverable - it's a scam!
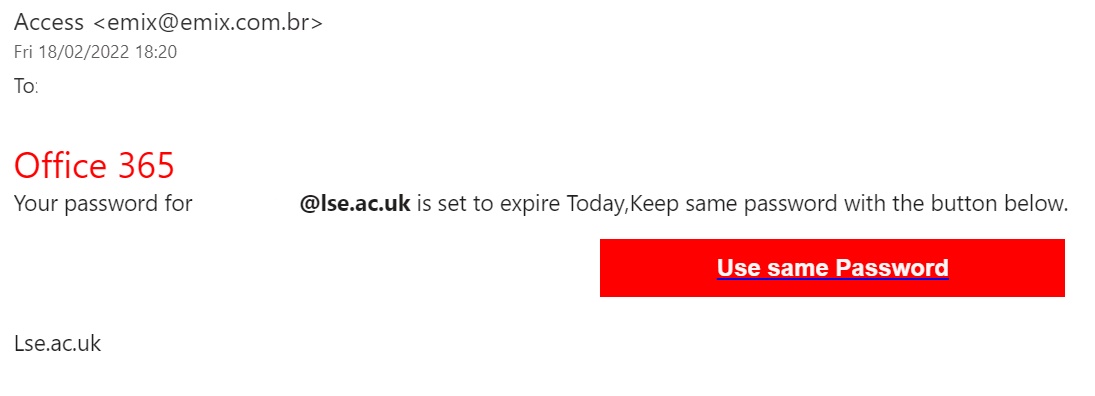
Microsoft Teams Phishing
As we continue hybrid learning and working, be aware that bad actors are increasingly sending Microsoft Teams phishing.
Tip: Look for wonky characters & fonts, typos, and blurry graphics.
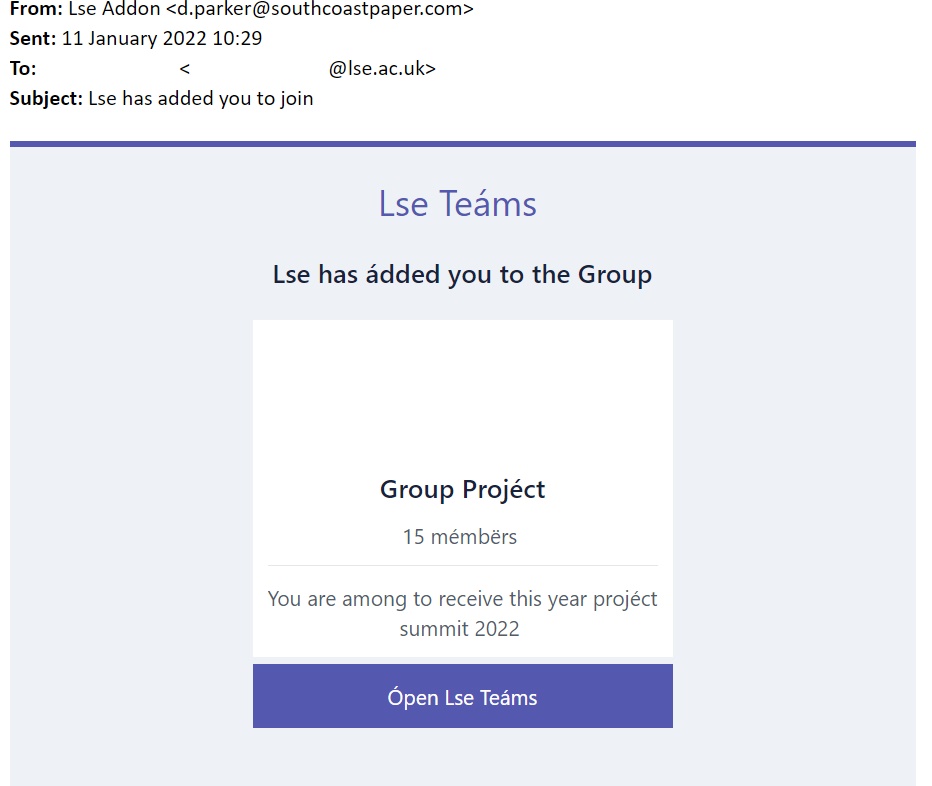
DocuSign Phishing
DocuSign is commonly used for sending and receiving digital signatures for imporant paperwork. Unfortunatey, this software is frequently spoofed by bad actors to send phishing links.
Tip: Think twice if an email asks you to click on a link to view a document
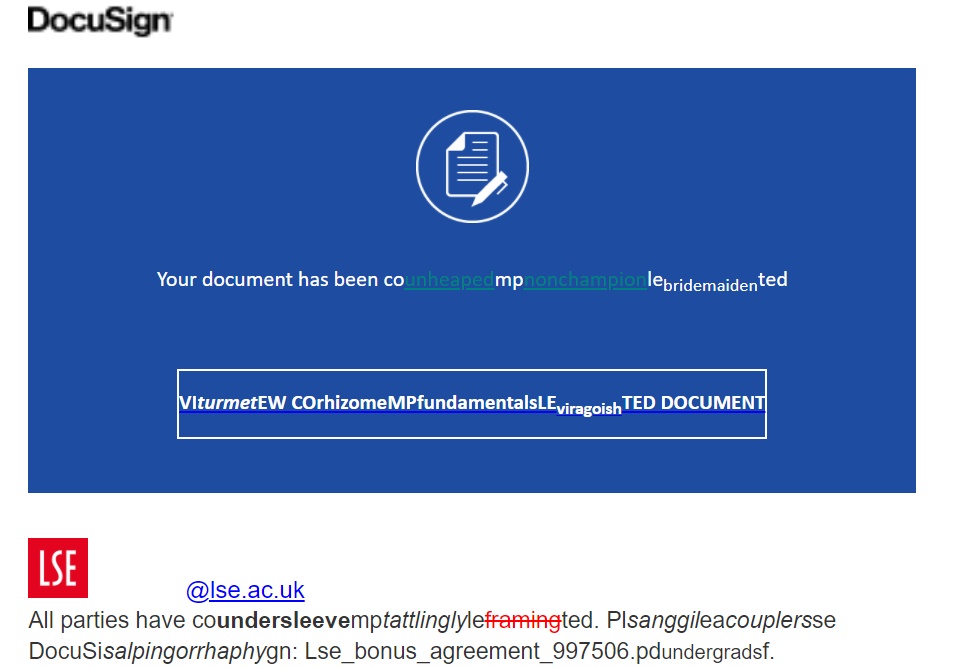
Spoofing
Did you know that phishing pretending to be someone else - typically a more senior colleague - is called spoofing? In this example, the sender calls the recipient by their given name and forges the spoofed user's signature to encourage a quick reply.
Tip: Gmail is a popular email domain used to spoof
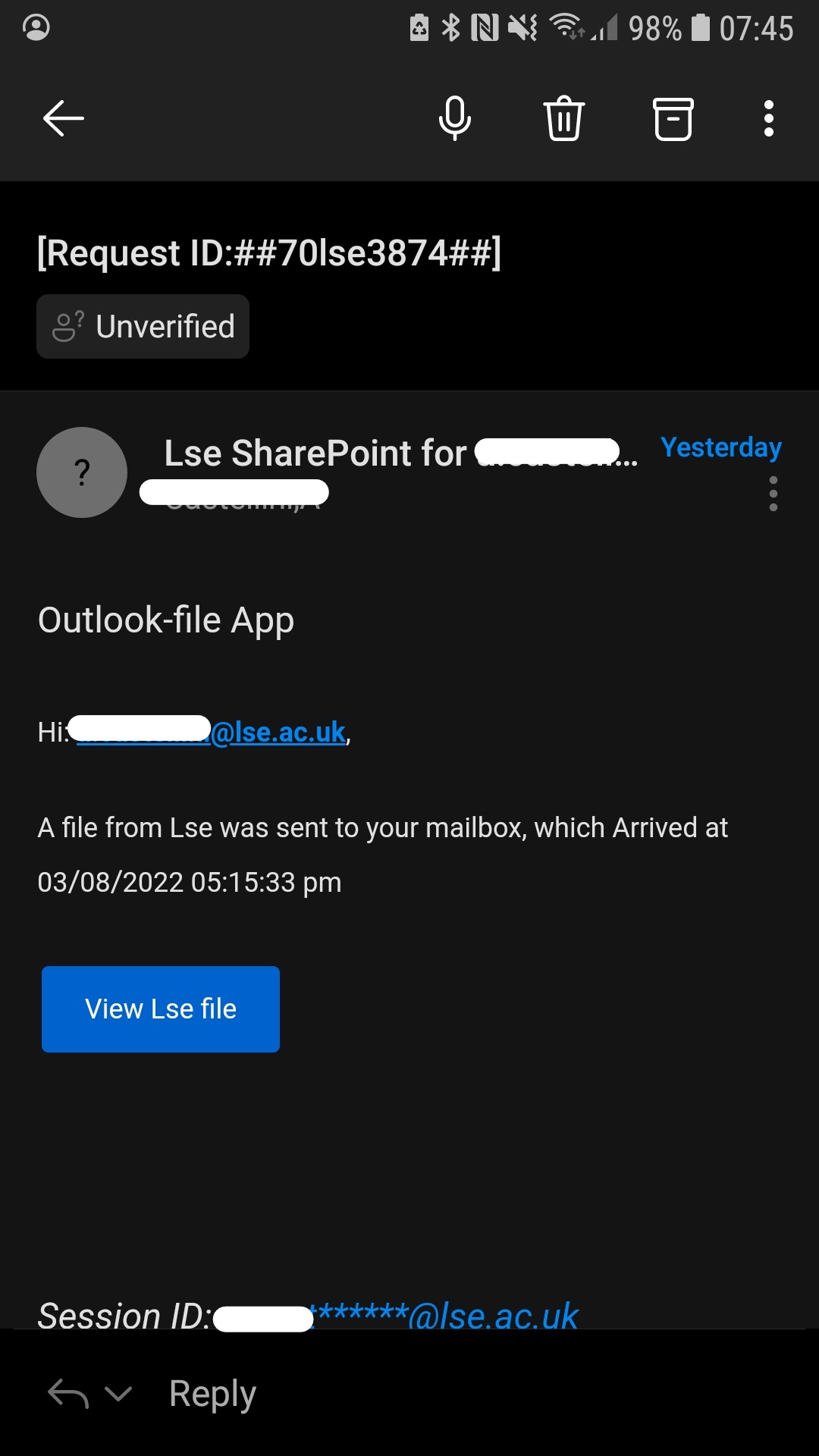
Spoofing Emails on your Phone
Spoofing can be even harder to spot when you're on the go and checking your phone. Mail apps often minimize the sender's full email address, as seen in this SharePoint phishing example.
Tip: Avoid clicking on a link on your phone & wait until your in your office/on campus/at home again to read the full message & double check the sender
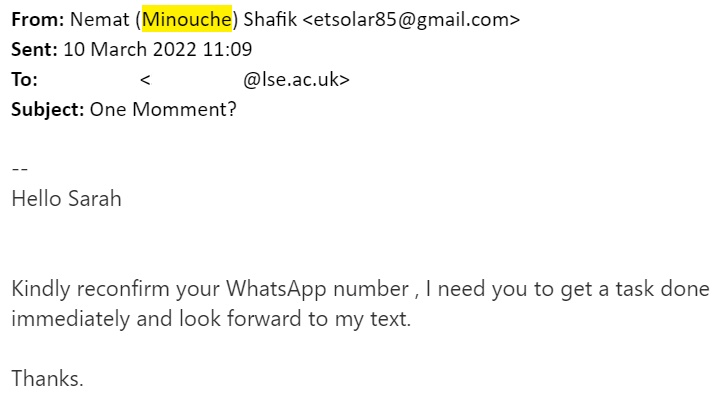
Whaling
Did you know that the bigger the phish, the more we call it a "whale"? Whaling is a type of phishing that spoofs high-ranked individuals (CEO/CIO, directors) who are at the top of an organisation's hierarchy.
Tip: the odds that the School's Director wants your WhatsApp to buy a gift card are, quite frankly, very low.
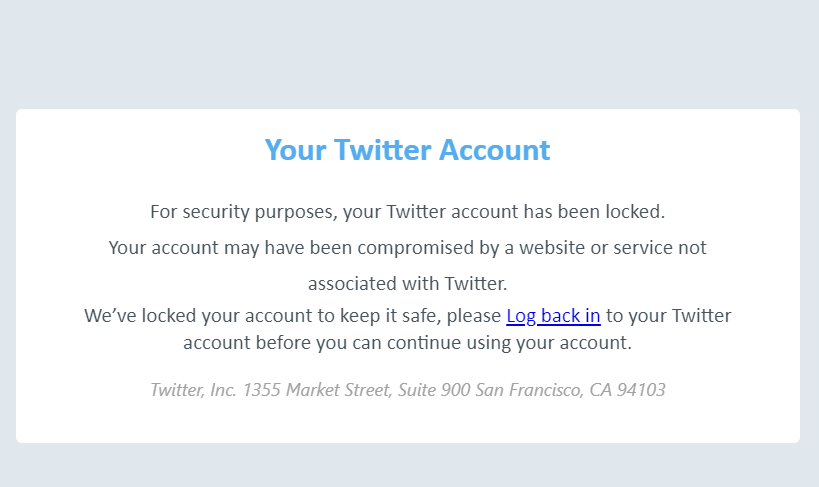
Twitter Phishing
You could receive phishing pretending to be from Facebook, Twitter, Instagram, TikTok, Snapchat and LinkedIn. This example wants you to click the hyperlink and enter your LSE or personal credentials.
Tip: Check your social media app. If you don't have issues using Twitter, there's no reason your profile should be blocked "for security reasons"
Voicemail phishing
If you're not expecting a voicemail, don't fall for voicemail phishing emails! These are an older but nevertheless persistent type of phishing to stay aware of. We've also received reports of FAX phishing.
Tip: Legitimate LSE voicemails should only be emailed from <voicemail@lse.ac.uk>.

DropBox Phishing
The School does not recommend using DropBox, because it's not GDPR-compliant. You won't receive a DropBox email from LSE. And a third party sender asking you to click on a link to view a document is suspicious, like in this example.
Tip: A mixture of different fonts, underlined words, and different text colors are typical indicators of a fake message.

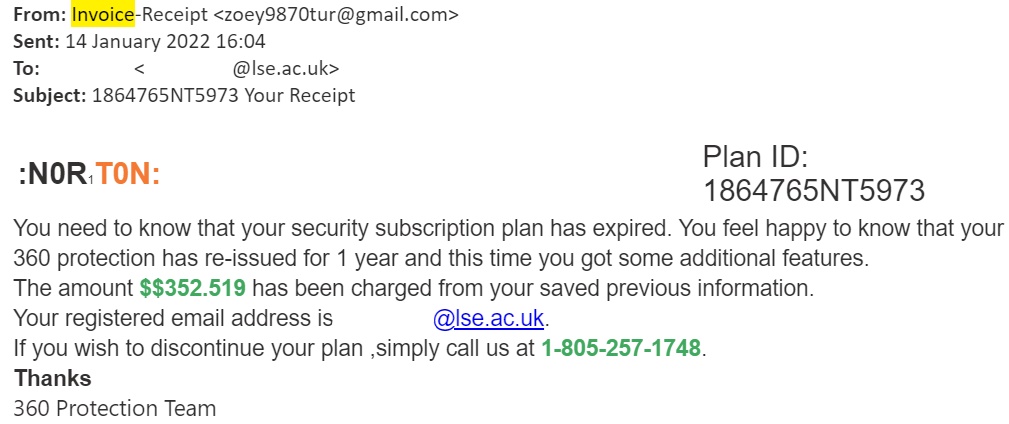
Anti-Virus Phishing
Bad actors have even preyed on users who want to be cyber secure and use an anti-virus (AV) software. In this example, the sender is spoofing Norton, and if a user calls the 1-800 number they will most likely be asked for personally-identifiable information and credit card/bank details.
MalwareBytes, Avast, and McAfee are other commonly used AV software that could be spoofed.
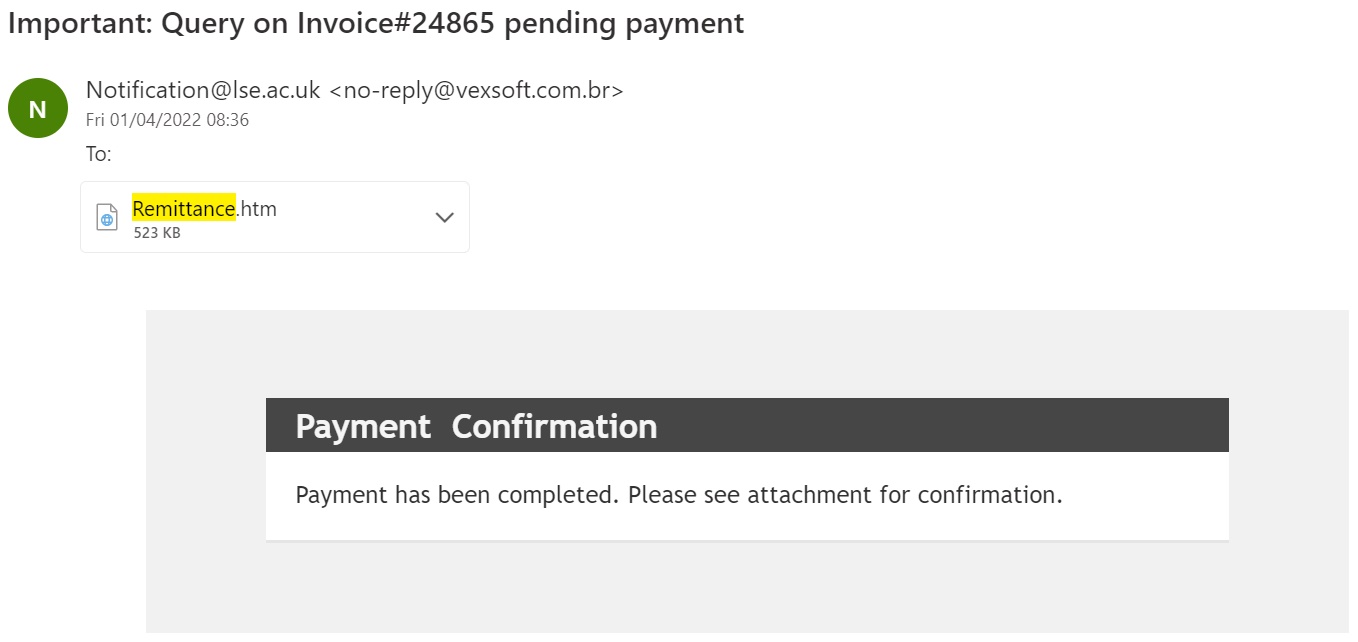
Remittance Phishing
This increasingly pervasive species of phish claims you're receiving money, and all you have to do is download the attachment/click the link. These emails may look very simple, but the social engineering is powerful - everyone wants to receive a payment!
Tip: Don't reply! Check your OneFinance or contact the School's Finance Division using their web enquiry formhttps://lse360.my.salesforce-sites.com/form?formid=217915. Please do not contact the DTS (IT) Service Desk with queries about OneFinance.
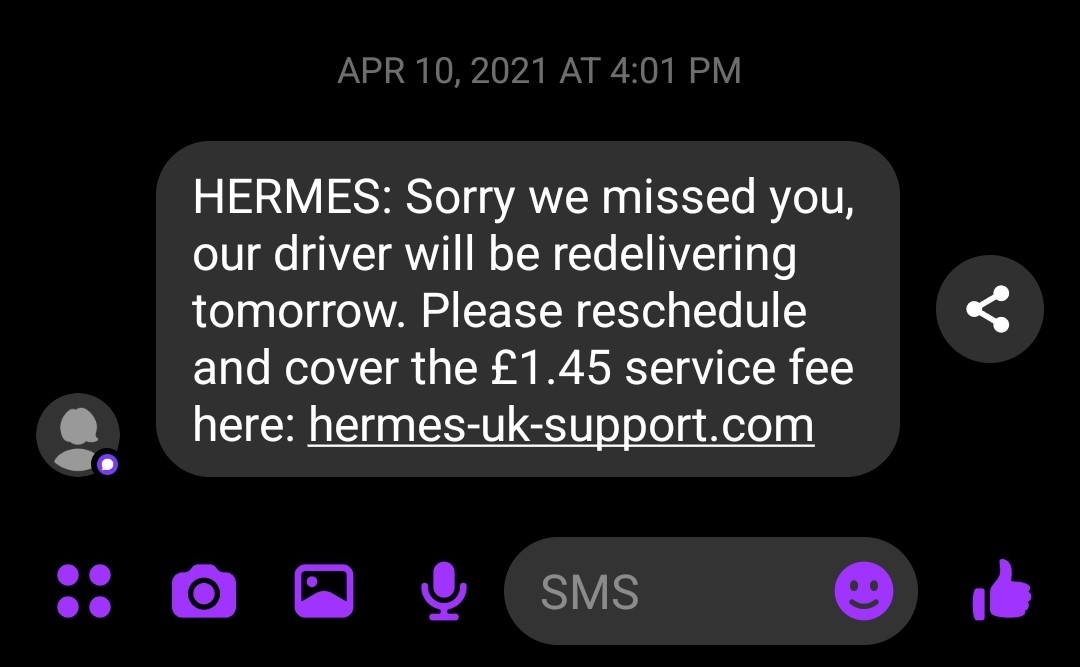
Smishing
When you get an SMS/text message that's phishing, we call that "smishing" This can be a very tricky phish to catch - I once receive smishing from "Evri" (the new name for Hermes parcel delivery service) the same day I received a legitimate delivery from Evri.
Tip: You should never owe money (£2.99/$3.99 etc.) in order to receive a package. If you did, you already paid shipping when you ordered the item. Ignore & block the number.
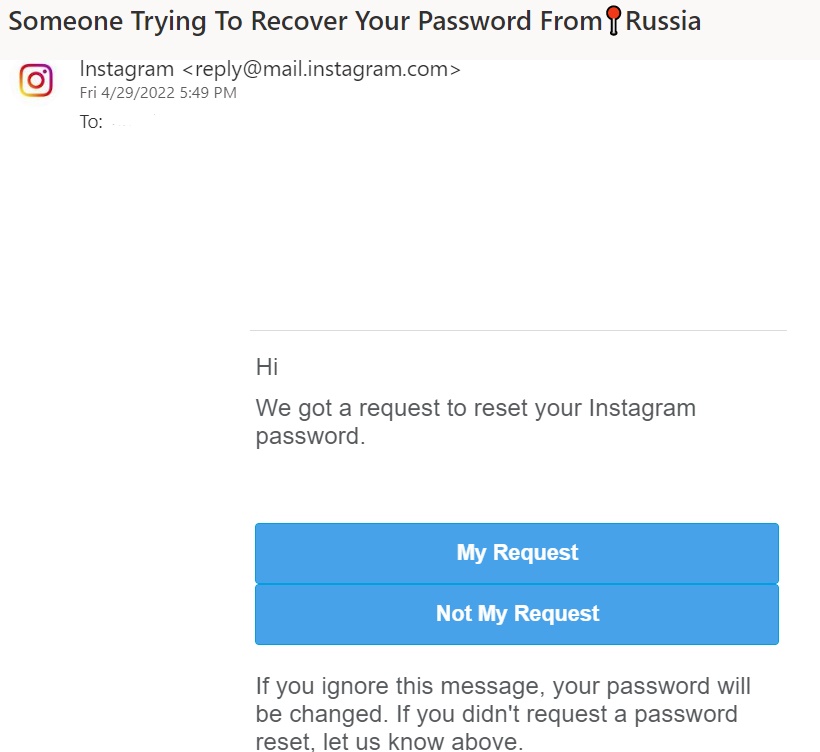
Instagram Phishing
Bad actors are aware you may be using multiple social media platforms, and they're targetting those accounts with fake "Your password's expiring", "Geographically improbably logins", or "Your account's violated community guidelines".
Tip: Real social media platforms (FaceBook, WhatsApp, Instagram, TikTok, etc.) may send you an email notifying you of a recent login (time and IP address). But they will never ask you to login and enter your password!
Transferwise/Wise phishing
In this example, the bad actor wants you to click on the blue hyperlink 'Go to your account' and provide your credentials to access your Wise (formerly Transferwise) bank account.
The message says you need to click the link to secure your account - ironic, because falling for this phishing email would compromise any money held in this Wise account!

Fax phishing
A fax is the telephonic transmission of scanned printed documents, which are sent from a sender's fax machine to a recipient's telephone number associated with a receiving fax machine, which then prints the document.
This is an older technology, and you should not be expecting to receive a fax document at LSE! 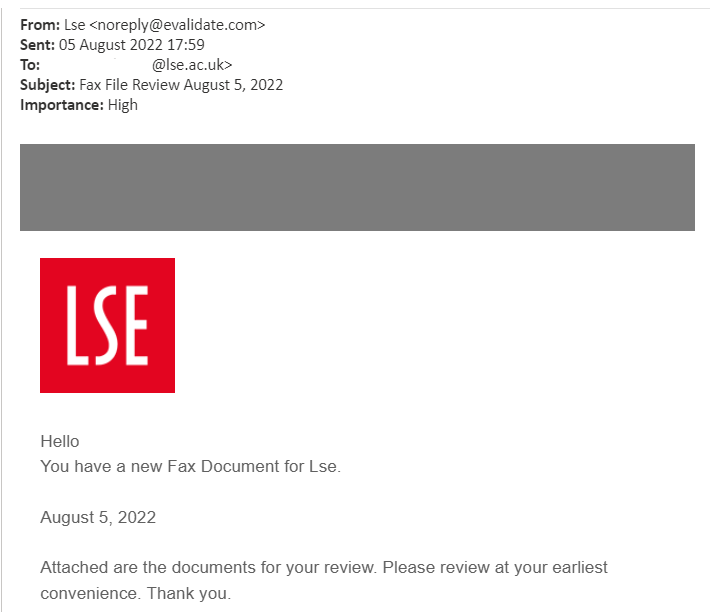
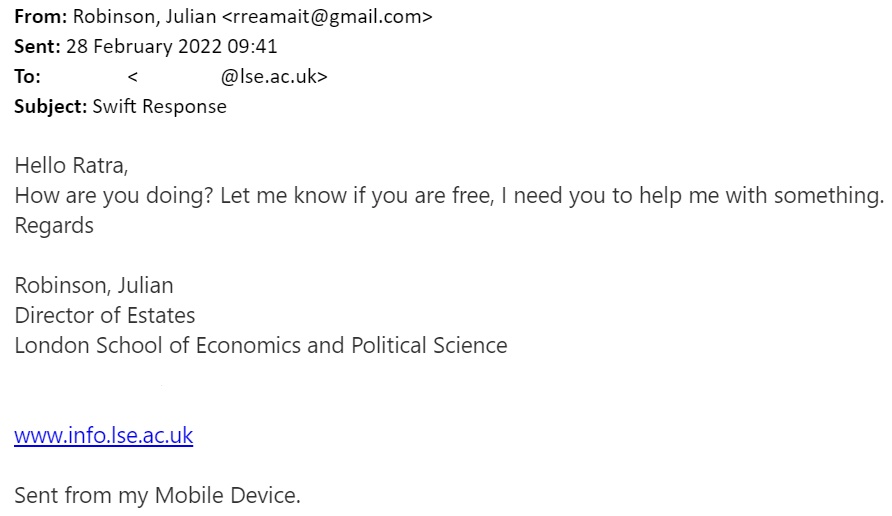
Spoofed recipient phishing
Ever wondered what you would do if you saw an email sent from yourself to yourself, and you know you didn't send it??
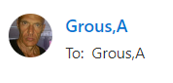
This is a very common scare tactic of social engineering. A bad actor has "spoofed" your email address, so they can lie that they have compromised your LSE account. Recipient spoofing can try to steal your LSE credentials. It is also frequently used to blackmail people, to lie about compromising your device and using your web camera to spy on you, in order to extort money.
Please remember - this is not true. An email header can be manipulated to make it appear like your LSE account emailed itself, but this didn't happen. It's a lie and you should not feel threatened.
If you ever see an email like this example in your LSE inbox, let us know asap at phishing@lse.ac.uk
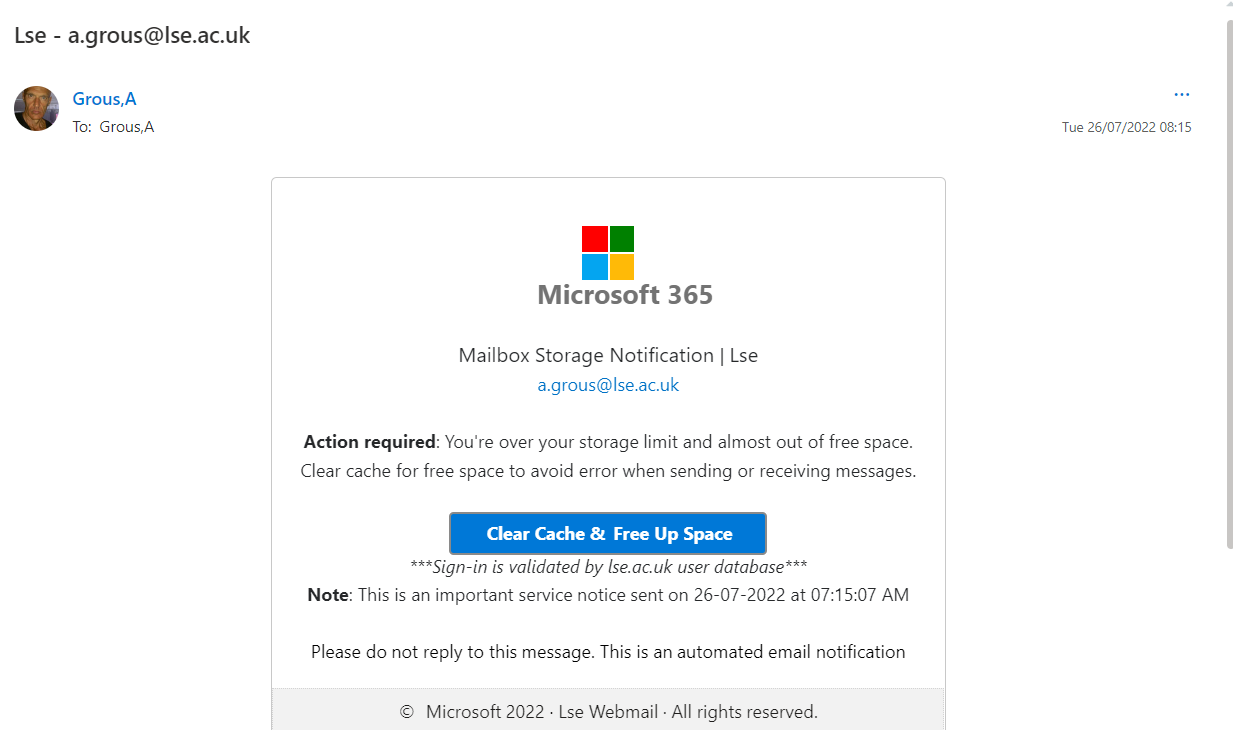
Clean up your LSE storage phishing
Similar to our earlier advice about "changing your password" phishing - LSE will never email you to say you've run out of account storage. This tactic wants to make you worry about losing access to your data, so you'll input your LSE credentials more quickly and without asking questions.
If you fall for this type of phishing, change your password immediately and contact phishing@lse.ac.uk
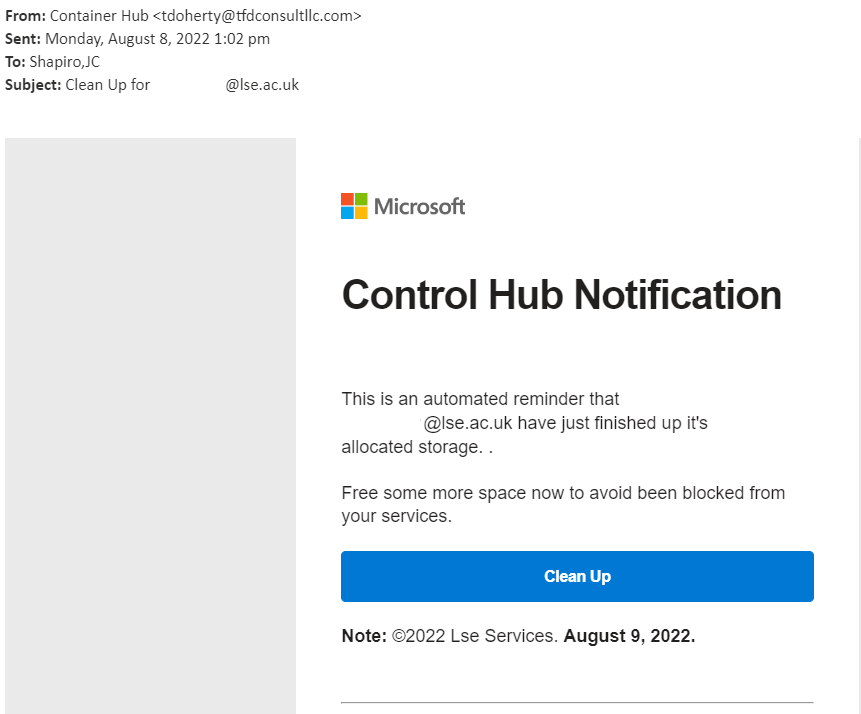
Ghostwriting phishing
Academic integrity may not seem like a typical cyber security topic - we focus on protecting your data and account security. But scams targetting the higher education sector are pervasive, and it's important to recognise them and report them like you would any other phishing.
In this example, a student reported receiving an email offering ghostwriting services. There are many ethical issues here and also cyber security risks from clicking on the email - you could compromise your LSE account, viruses could infect your devices, your data could be locked with ransomware, and your personally-identifiable information, including payment details, could be stolen.
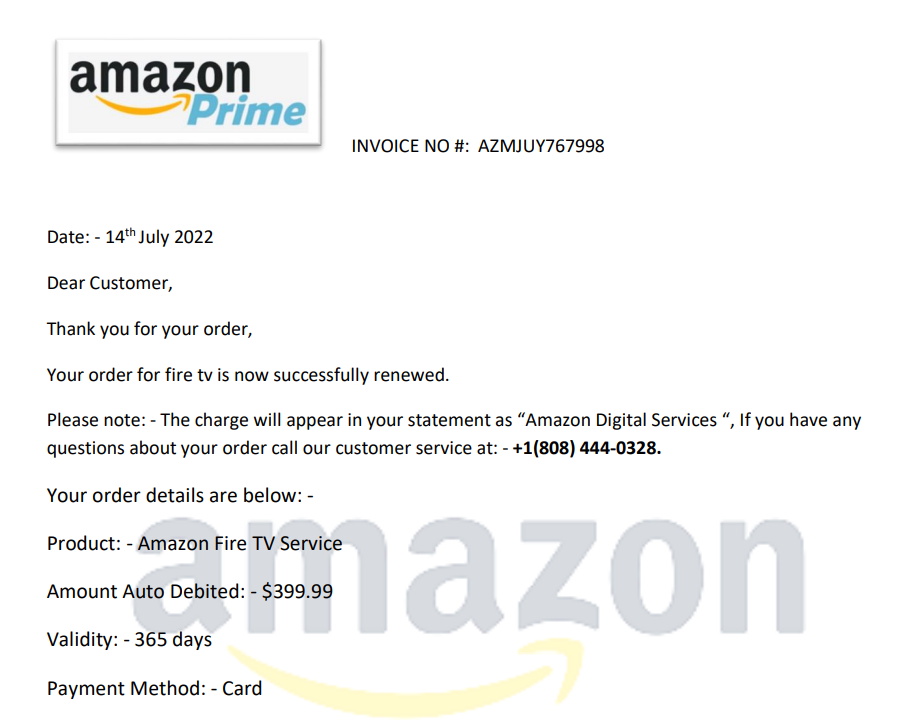
Amazon Prime phishing
Bad actors are following our online spending habits - and crafting phishing emails that look like an Amazon Prime bill.
Let's analyse this example of social engineering to understand potentially how manipulative it is. You can see it asks you to call a phone number for more information.This tactic preys on anyone who isn't very tech saavy and would prefer a phone call over online chats/emails. It says a large payment has been charged, which would cause anyone alarm, and espeically in the ongoing cost of living crisis.
What would happen if you called the number? In this case, they would most likely be spoofing Amazon customer service. The bad actor can record your voice and use it for other fraudulent purposes later. They may ask you how your day has been, and try to engage in a conversation to make you feel more comfortable. Alternatively, they can be abrasive and threaten you that the card payment won't be cancelled unless you share details immediately - at which point, they begin asking you to share credit card/bank details, your billing address, and other personally-identifiable information to "confirm" the Amazon purchase.
Remember that social engineering is very deceptive - and the right phish at the wrong time will catch anyone. Be extra careful! Phish can start with an email AND they can continue over phone calls.
Want to Know More?
Learn more about phishing and how to spot it in our Iron Rule 1: Beware of Phishing