
16 May 2023
The Microsoft Authenticator app has recently incorporated a new security feature- number matching. This update is being rolled out by Microsoft and LSE has no control over it, however this article explains what you can expect and why this new feature provides extra security for your account.
You may have noticed this already when logging into your LSE accounts that the Authenticator app now requests you to enter a number. This number will appear on the computer screen that you are logging in from. To complete the MFA approval process, enter the two-digit number from the screen that you are logging in from into your Authenticator app and confirm by pressing ‘YES’.
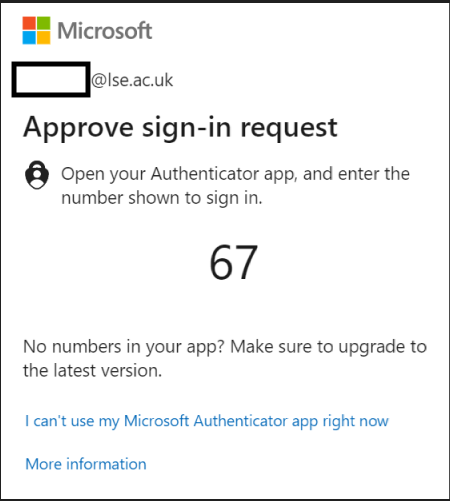
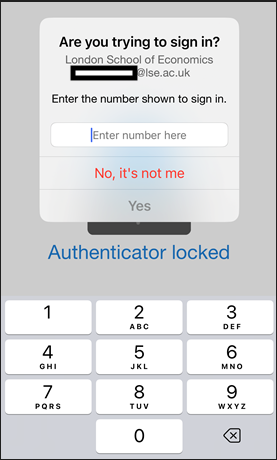
This extra step takes minimal extra time for users but will add an important layer of protection to against hackers. This will prevent instances of MFA ‘Prompt Bombing’ which we previously written an article about on our cyber security blog:
https://info.lse.ac.uk/staff/divisions/dts/services/infosec/MFA-Prompt-Bombing
The number matching feature creates a two-way system of authentication between the device on which your authenticator app is installed and the device that you are logging in from, so you can only type the number when you yourself are trying to login to your account. Hence, attackers can no longer use prompt bombing in the hope that you will confirm a request when not paying attention.
Can I opt out?
LSE cannot opt out or delay the “number matching” method, it is a new requirement for all Microsoft tenancies. LSE staff and students may not notice any immediate change due to remembered sessions that may continue for a few weeks but will eventually encounter the new extra step in MFA described by Microsoft as “number matching”.
Why is Microsoft introducing “number matching”?
Number matching is a key security upgrade – it will help defend against MFA attacks and prevent accidental login approvals. This is especially important due to the rise in “MFA bombing” – when a bad actor spam users with continuous requests in the hopes that they will accept one to stop the constant MFA push notification pop-ups “bombing” their phone screen.
What do I need to do?
Staff and students do not need to take any specific actions if already using the Microsoft Authenticator App, just ensure Notifications through mobile app is enabled in your Security Info settings here.
If you are still using SMS/phone calls for your primary MFA method, now is a great time to set up the Authenticator App. Please download the app from the App Store or Google Play and follow these instructions.